Security Research & Analysis
Technical documentation focused on real-world security incidents, vulnerability research, and offensive security techniques.
Research by Sohan Kanna | Security Researcher
Latest Updates
View Archives
Unpatchable? How Chinese Hackers Hid in Dell VMs for 2 Years Using "Magic Packets"
A deep dive into the critical Dell 0-day. How Chinese hackers used "Ghost NICs" and invisible malware to hide in corporate networks.
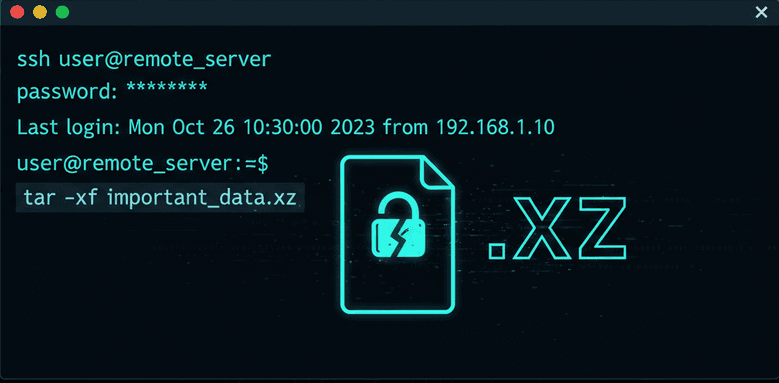
The XZ Backdoor (CVE-2024–3094): How a Supply Chain Attack Nearly Compromised Every Linux Server
A breakdown of CVE-2024–3094, how the attacker hijacked liblzma, and why this almost became the biggest supply chain compromise in Linux history.

The "Dumb" Editor That Got Too Smart: When Feature Bloat Leads to RCE
Notepad was supposed to be the safe harbor of Windows utilities. Then Microsoft added Markdown, and things got complicated.
The Invisible Siege: Why Modern APTs Have Weaponized the Operating System
The era of "smash-and-grab" malware attacks is fading among state-sponsored actors. Today’s Advanced Persistent Threats (APTs) have shifted toward a "Living-off-the-Land" (LotL) paradigm.

Hiding in Plain Sight: Deconstructing the UPSTYLE Backdoor (CVE-2024-3400)
A technical deep dive into the UPSTYLE malware and the CVE-2024-3400 vulnerability. This analysis dissects the malware's three-stage Python payload, its novel "living-off-the-land" C2 communication, and provides actionable IOCs for defenders.
The Notepad++ Hack: A Deep Dive Into a State-Sponsored Supply Chain Attack
How a beloved code editor was turned into a delivery mechanism for sophisticated spyware, and what it teaches us about modern cybersecurity threats.